PCI DSS Compliance for dummies
/in Knowledge, News【PCI DSS Compliance for dummies】
Even Cybersecurity Beginners Can Achieve Compliance
Top 5 questions asked (2W3H), when 1st time required by an acquirer or supervisor to obtain PCI DSS certification.
As the booming growth of e-commerce, remote work, and delivery platforms continues into 2024, the usage of cross-border transactions and online payments has accelerated, making payment card information security increasingly critical.
To protect cardholder personal information, the Payment Card Industry Security Standards Council (PCI SSC) mandates that all entities storing, processing, or transmitting cardholder data must comply with PCI DSS requirements.
The 12 core requirements and their sub-requirements within PCI DSS are designed to protect cardholder data.
When your acquiring bank, regulatory authority or boss requires you to obtain PCI DSS certification, and you’re unsure where to start, you might ask the following five key questions (2W3H):
Table of Contents
What is PCI DSS ?
PCI DSS stands for Payment Card Industry Data Security Standards, which is established and managed by the international organization, Payment Card Industry Security Standard Council (PCI SSC). These standards are specially designed to protect payment card data from unauthorized access and misuse.
PCI SSC comprises major global credit card organizations, including American Express, Discover Financial Services, JCB, MasterCard, Visa Inc., and China UnionPay.
PCI DSS standards are a set of industry-wide guidelines, focused on securing cardholder information across these brands. These standards apply to all entities, which store, process, or transmit cardholder data. Merchants or service providers handling payment cards from these brands, regardless of their size or transaction volume, are all required to follow and comply with PCI DSS to ensure the security of cardholder information.
Who needs PCI DSS Certification?
Any organization that stores, processes, or transmits cardholder data is required to comply with PCI DSS Standards. Depending on how an organization handles cardholder data, they are categorized into different types and levels.
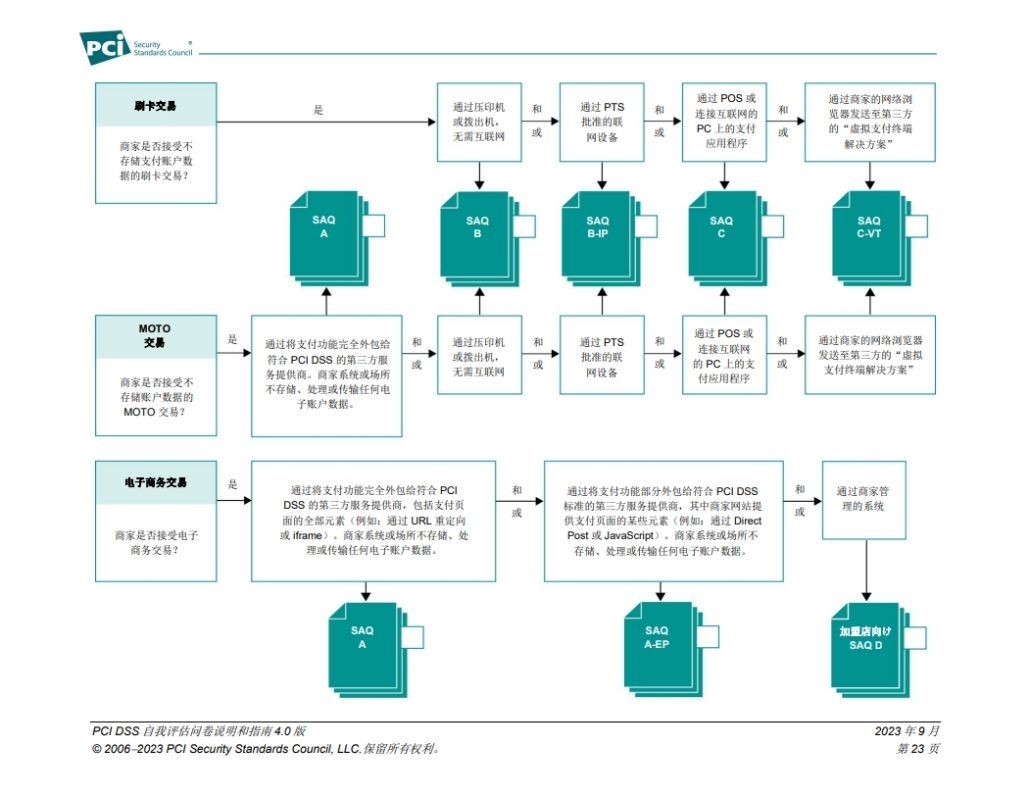
Step 1: To determine whether the entity is a Merchant or Service Provider.
Merchants
Organizations that accept payment cards in exchange for goods or services. This category includes physical stores, online stores, and those offering downloadable virtual goods or services.
Service Providers
Entities that transmit, process, or store payment cardholder data as part of services they offer, or that can control or influence the security of cardholder data, including third-party payment processors, payment gateway providers, wallet service providers, and online marketplaces. Data centers and cloud service providers offering virtual hosting services also belong to this category.
Step 2: Once determining whether your organization is a Merchant or a Service Provider, you can further identify the PCI DSS level.
Level 1 Merchants and Service Providers
require an on-site assessment by a Qualified Security Assessor (QSA), who will conduct the review and provide a report.
Level 2-4 Merchants and Level 2 Service Providers
can use the PCI DSS Self-Assessment Questionnaire (SAQ) to perform a self-assessment, or they can seek assistance from a QSA to ensure a faster and more accurate evaluation.
Who can assist PCI DSS Certification?
For Level 1 Merchants or Service Providers undergoing their first PCI DSS assessment, it is advisable to seek professional guidance.
QSA (Qualified Security Assessor)
is a professional authorized by PCI SSC, trained and certified to conduct PCI DSS assessments and provide Reports on Compliance (ROC) and Attestations of Compliance (AOC). QSAs must regularly update their certification to stay current with the latest PCI DSS versions. If your organization is a Level 1 Merchant or Service Provider, an on-site assessment by a QSA is mandatory.
QSAC (Qualified Security Assessor Company)
employs QSAs and provides expert assessment and consulting services. QSAC can assist you in understanding the specific requirements of PCI DSS and guide you in establishing a secure Payment environment.
How to choose QSA and QSAC?
Visit [PCI Security Standards Council] to verify the certified QSA and QSAC.
- Inquire peers or partners about their experience and recommendations that already completed PCI DSS Assessment.
- Review customer evaluations and case studies of potential QSAs and QSACs to ensure their experience and expertise.
- Consultation Services: Conduct initial consultations with multiple QSAs or QSACs to understand their service scope, fee, and work process.
By following these steps, you can find a suitable QSA or QSAC to assist your PCI DSS Assessment, ensuring the payment environment is secure and compliant.
How to do?
PCI DSS Compliance Assessment normally consists of 4 main stages:
1. Preparation Stage
Scope Confirmation and Consulting phase.
**Scope Confirmation**
- Preliminary Assessment: Evaluate existing security measures to identify gaps and scope needing adjustment.
- Define Assessment Scope: Determine systems, networks, and applications that need to comply with PCI DSS standards.
**Consultation Phase**
- Engage Consultant or QSA: Select a Qualified Security Assessor (QSA) or Qualified Security Assessor Company (QSAC) to assist in verifying environment compliance, guiding remediation processes, and scheduling Assessment.
- Security Training: Provide employees with relevant security training to enhance overall security awareness.
2. Data Preparation Phase
Preparation and Implementation of Necessary Controls
**Data Preparation**
● Policies and Procedures: Develop and update security policies and operational procedures to ensure PCI DSS compliance.
● Document Collection: Gather and organize all required documents and evidence to demonstrate compliance.
3. Assessment Phase
QSA Conducts On-Site Assessment.
**Audit Execution**
● Internal Assessment: Conduct internal reviews before formal Assessment to ensure all issues are addressed.
● On-Site Assessment: Conduct on-site Assessment led by QSA to verify consistency between actual operations and documented practices.
4. Report Phase
QSA Writes and Submits Compliance Reports and Certifications
● Report Writing: QSA writes Report on Compliance (ROC) and Attestations of Compliance (AOC).
● Report Submission: You can submit a report to the Payment Card Organization or Acquirer.
● Certification Issuance: You will receive compliance certifications indicating adherence to PCI DSS standards from QSAC.
How long does it take?
The overall timeline for achieving PCI DSS compliance certification, from initial environment verification to providing final reports, is about 3 to 5 months. Main stages of Compliance Certification Process are listed below:
Preparation Stage(1-2 months):Environment Verification and Consultation Phase.
Data Preparation Stage (1 month): Preparation and Implementation of necessary Control Measures.
Assessment Stage (5-7 days): On-site Assessment conducted by QSA.
Report Stage (0.5-1 month): QSA writes and submits Compliance Reports and Certifications.
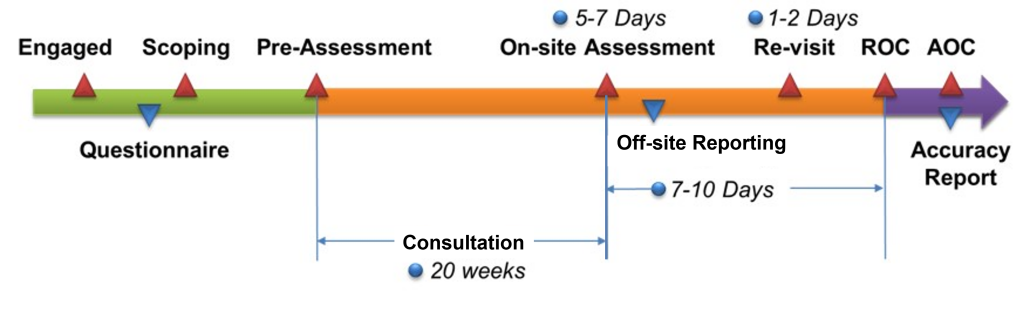
Actual timelines may vary due to the following factors:
- Preparedness: The extent of preparation before certification can expedite the process.
- Complexity of Systems and Operations: The complexity of IT environments, network architecture, and operational processes can affect certification timelines.
- Resources invested by the company (including manpower, time, and budget) and efficiency in project management.
To ensure an efficient process, it is recommended to:
- Begin preparation: As early as possible, especially organizing documents and policies.
- Effective Communication: Maintain close communication with QSA throughout the certification process to promptly address any issues that arises.
- Continuous monitoring: After certification, it is necessary to continue maintaining and improving security measures to ensure long-term compliance with PCI DSS requirements.
How much does it cost?
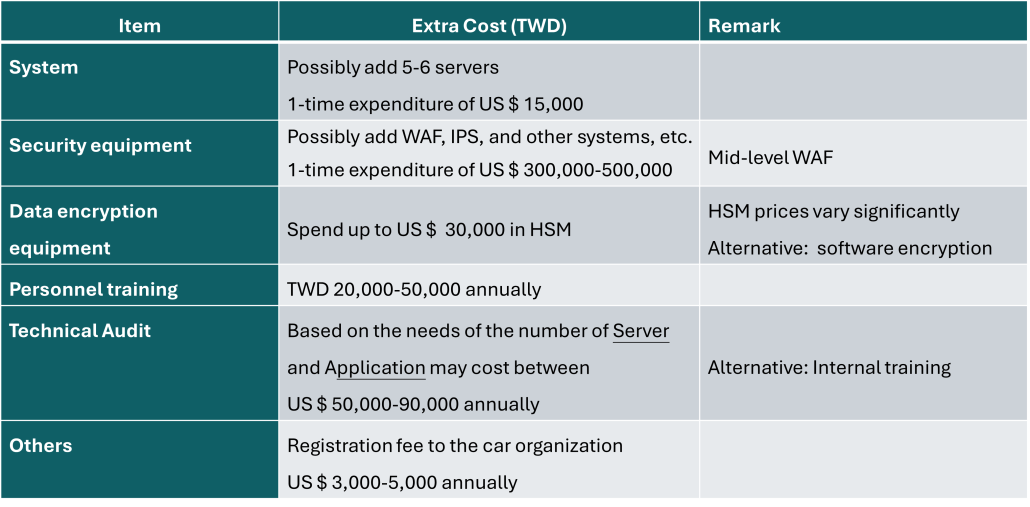
Estimated Additional Costs for 1st-time PCI DSS Compliance
A. System
Due to the high-security requirements of PCI DSS, certain systems may need to be separated to comply with requirements such as having only one primary function per system component (Req. 2.2.3). Previously, functions like Web Server, Application Server, and DB Server might have been on one machine but now need to be split, potentially requiring additional server equipment (virtual servers can be used).Additionally, security components like NTP Servers, FIM Servers (File Integrity Management), and Log Servers may be needed to meet compliance, potentially increasing the number of required machines compared to before.
B. Security Equipment
Meeting PCI DSS security requirements may necessitate purchasing additional security equipment such as Network Security Control devices (NSCs) like firewalls, Intrusion Prevention Systems (IPS), Intrusion Detection Systems (IDS), and Web Application Firewalls (WAF).
C. Data Encryption Equipment
Organizations with high security and performance demands may opt for Hardware Security Modules (HSMs) to encrypt card data securely as required by PCI DSS.
D. Personnel Training
PPCI DSS mandates training for personnel including awareness training, secure coding training, and conducting drills for Incident Response Plans (IRP). If staff perform Vulnerability Scans or Penetration Tests, they will also require adequate security training, potentially increasing training costs.
E. Technical Test
PCI DSS requires various periodic technical tests including Internal Vulnerability Scans, External Vulnerability Scans (ASV), Internal and External Penetration Tests, Wireless Scans, Card Number Scans, and Code Reviews. This section typically incurs additional expenses.
F. Other
If you are a service provider, acquiring institutions or card organizations may require registration in their service provider registries like VISA Registry or MasterCard SDP (Service Provider Registration).
For a small to medium-sized Service Provider without prior PCI DSS compliance experience, the estimated additional expenses might include as listed below:
PCI DSS Certification Costs
In addition to the potential additional costs mentioned above, the cost of PCI DSS Assessment can be varied with the time required by PCI DSS QSAs to complete the Assessment and Report.
The estimated assessment time depends on the following factors:
System Complexity: The number of hosts, types of operating systems used, components installed on systems, multiple OS configurations, and security configurations all affect the sampling required during audits and increase audit time.
Security Equipment and Networks: The number of security devices within the assessment scope such as Firewalls, IPS, IDS, WAF, Switches, Routers, SIEM, DRP, etc., requires configuration, updates, access control checks, logging, and more, thereby increasing assessment time with more devices and complex network planning.
Connections to Acquiring Institutions and Service Providers: More connections to acquiring institutions and service providers form more complex data flows (Dataflows), necessitating additional time for inspection.
Database and Card Data Storage and Encryption Methods: Diverse card data flows and storage methods require more encryption or security measures, resulting in additional inspection items.
Number of Operational Units: The number of stores, data centers, and operational offices increases the days required for Assessment, e.g., banks, telecom companies, and businesses with numerous stores and offices with extensive sampling. Moreover, backup data centers storing card data are also included in the scope.
Generally speaking, PCI DSS Assessment costs vary by region due to different annual fees set by the PCI SSC and varying salaries for QSAs in different regions. In Southeast Asia, e.g., a small to medium-sized service provider requires 3-5 days for on-site Assessment and around a week for report compilation. Excluding travel costs, PCI DSS certification costs typically range between NT$400,000 to NT$600,000.
However, an actual quotation depends on the complexity factors mentioned above.
Whether you are a cross-border e-commerce business, a third-party payment platform, or a service provider, adhering to PCI DSS compliance requirements is crucial. Implementing these compliance measures not only provides your acquiring bank and regulatory authorities with a certificate of compliance but also directly helps your business reduce the risk of data breaches and theft while enhancing consumer confidence in the security of their transactions.
PCI DSS compliance consists of over 400 requirements, covering everything from understanding and interpreting the standards, providing evidence, and obtaining certification, to maintaining compliance in the future. How do you ensure ongoing compliance?
It is recommended to consider hiring a QSAC (Qualified Security Assessor Company) to help you quickly and effectively achieve compliance in a short time.
After certification, you can utilize a compliance management system offering features such as automated monitoring, alerts, regular data submission, and real-time visual status updates. This ensures that your business remains compliant and secure at all times.
*For more information about PCI Compliance Services, please feel free to contact us.